Who is it for
Security leadershipDesigning or maturing ISMS programs.
Executive reportingOrganizations needing governance and reporting that is leadership-ready.
Enterprise alignmentAligning security, compliance, and incident response.
Design, mature, or modernize your security program with governance that stays audit-ready and aligned to day-to-day operations.
Security leadershipDesigning or maturing ISMS programs.
Executive reportingOrganizations needing governance and reporting that is leadership-ready.
Enterprise alignmentAligning security, compliance, and incident response.
Weekly working sessions and monthly governance reviews.
vCISO leadership, GRC analysts, incident response specialists.
Summaries of each managed program component and leadership option.
Builds a formal security program aligned to frameworks like SCF, NIST, or ISO for consistent controls and audit readiness.
Establishes risk management to identify, prioritize, and mitigate security risk with a risk-informed culture and tracking.
Manages third-party risk by aligning vendor practices to risk tolerance, contractual controls, and regulatory expectations.
Delivers response planning and incident command services with clear roles, escalation paths, and coordinated recovery.
Executive security leadership integrated with your team to shape strategy, guide decisions, and oversee compliance.
Flexible senior CISO support as staff augmentation for organizations that do not need a full-time executive.
Core security governance capabilities mapped to common regulatory and assurance frameworks.
| Standards alignment focus | ISO 27001 | SOC 2 | FedRAMP | CMMC | HITRUST | HIPAA |
|---|---|---|---|---|---|---|
| Security governance and defined program scope | ||||||
| Security policies, standards, and procedures approved and maintained | ||||||
| Asset inventory and data classification maintained | ||||||
| Risk assessment performed and tracked on a defined cadence | ||||||
| Change management and secure configuration baselines |
Design, mature, or modernize your information security and GRC program with proven frameworks and continuous operational alignment.
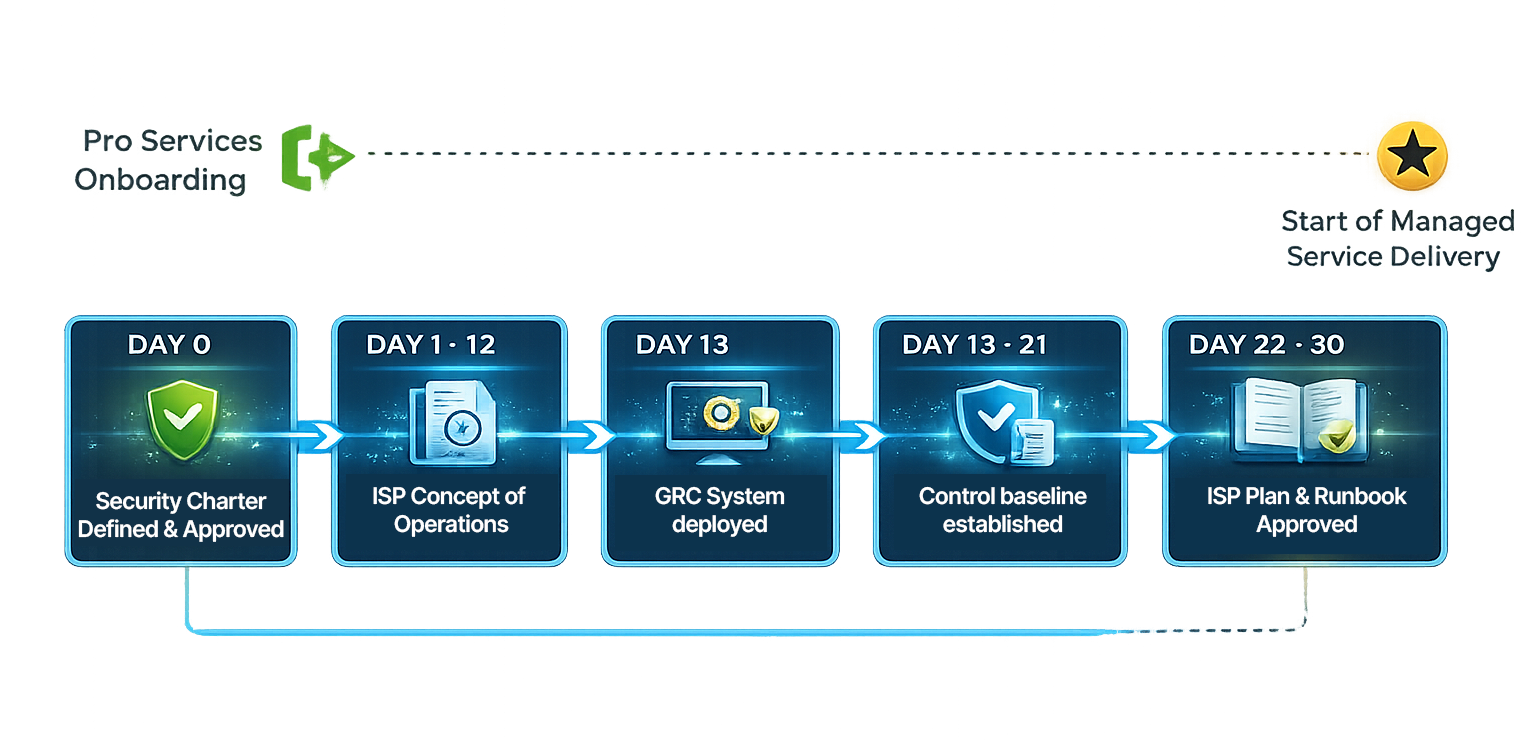
Representative artifacts produced during program build-out.



Request a consult or download the program overview.