Information Security Program
The ISG-ISP Managed Program creates a secure information environment aligned with your organization’s goals, operational needs, and compliance, focusing on transparency, consistency, and flexibility.
Enhance Your Security
Establish a modern & composable ISP
Get started
Fill in the form below and we will contact you ASAP. We endeavor to answer all inquiries within 24 hours on business days.
The ISG-ISP Managed Program builds a secure ISMS, aligning security with business goals, operations, and compliance while ensuring transparency and flexibility.
Policy Compliance
Publish & Maintain
Policies & Standards
Regularly update and enforce security policies for compliance.
-
Ensure alignment with regulations
-
Update policies as needed
-
Promote awareness across teams


Control Framework
Internal Control Baseline Development & Maintenance
Develop and implement security controls to mitigate risks.
-
Establish a strong security framework
-
Adapt controls from industry standards
-
Assign control owners for oversight
Exception Handling
Security Exception
Management
Streamline exception handling with a structured approval process.
-
Document and review security exceptions
-
Implement a digital request workflow
-
Manage exceptions until resolution


Leadership Insights
Senior Leadership & Board Communication
Ensure leaders stay informed on security risks and strategies.
-
Provide regular security updates
-
Align security with business goals
-
Facilitate informed decision-making
Executive Coaching
CISO Mentorship
Empower your CISOs with expert guidance and strategic insights.
-
Offer leadership coaching
-
Share industry best practices
-
Strengthen crisis management skills

Boost Efficiency and Security
Integrated with Your Microsoft 365
Seamlessly embedded in your Microsoft 365, our solutions enhance operations, security, and data integrity within your existing infrastructure.

Digital Policies &
Standards
Establish a secure, consistent digital governance framework for effective information management.
-
Ensure standards before publishing
-
Customize branded templates
-
Streamline approval process

Business Process & Service Inventory
Streamline operations by cataloging and managing critical business processes and services.
-
Map process & service dependencies
-
Identify key service relationships
-
Assign process-level risk ownership
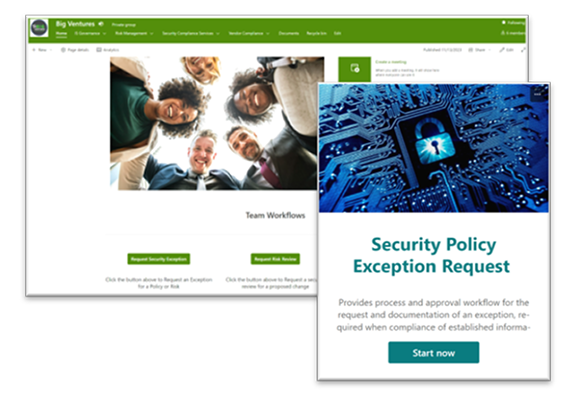
Security Exception Moderated Workflows
Ensure controlled risk management by systematically handling security policy exceptions.
-
Streamline workflows with data
-
Use MS Forms & SharePoint efficiently
-
Get reminders for exception reviews
Our Approach
Human-Centric
Security Management
Strengthen your security with expert leadership and ongoing collaboration for proactive protection.
Launch with ease
Transform Your Information
Security Programs
Schedule a session with a Client Success Specialist to elevate your security strategy and improve vendor management.
How it works
Easy process to bring your vision to life
A simple, effective approach to enhance your cybersecurity posture with precision and expertise.
Consultation
We analyze your security landscape, identify risks, and provide expert recommendations.
Implementation
Our team develops and deploys customized security solutions aligned with your needs.
Monitoring
We continuously monitor, refine, and enhance security measures for lasting protection.
Got a question?
Get in touch, and our experts will respond promptly to guide
you through the next steps and address vour needs.
Get started
Fill in the form below and we will contact you ASAP. We endeavor to answer all inquiries within 24 hours on business days.

3Hue provided exceptional expertise and guidance, giving us peace of mind about our cybersecurity.
John Doe
Trusted by Industry Leaders
Confidence in security starts with the right partner—one that understands your needs and delivers proactive solutions to keep your organization safe.
Exceptional 5-star rating
Partnering with 3Hue gave us the confidence & the know-how to tackle cybersecurity threats proactively.

Secure Your Business Today
Schedule a call to strengthen your cybersecurity with our integrated MDR and GRC solutions, ensuring compliance and proactive risk management.

